Authentication with OpenID
- name:
- OpenID Authentication
- description:
- SSO User authentication and User provisioning using oAuth or OpenID
- version:
- 2.1.0
- release:
- 2025-10-03
- itop-version-min:
- 3.2.1
- code:
- combodo-hybridauth
- state:
- stable
- php-version-max:
- PHP 8.2 since version 1.2.1. PHP 8.0 otherwise
With this extension, users can connect to iTop using OpenID providers (Facebook, Google, Twitter, LinkedIn, MicrosoftGraph …)
Features
Add capability to configure SSO authentication with most common OpenID Identity providers (Facebook, Google, Twitter, LinkedIn, MicrosoftGraph …)
-
It offers new authentication modes based on oAuth and OpenID Single Sign On (SSO) for the following OpenID providers:
-
Those modes can be mixed with other modes (internal, SAML …)
-
It is possible to configure several Identity providers if you want to allow access for instance to both Google and MicrosoftGraph
-
It relies on HybridAuth library library, which provides a unified interface to identify a user and retrieve contact information.
-
Some of those Identity providers are able to provide user information to allow automatic User and Person provisioning in iTop.
Check the third column of the Providers table, it is required for automatic User/Person provisioning on User first connection.
Revision History
| Release date | Version | Comments |
|---|---|---|
| 2025-10-03 | 2.1.0 | * N°8374 - Allow hybridauth to synchronize any attribute |
| 2025-07-21 | 2.0.0 | * Support authentication via OktaOIDC oAuth2
provider * N°8375 - Auto provisioning doesn't update contact/user |
| 2025-01-23 | 1.2.4 | * N°7807 - Add support for organization selection
during autoprovisioning * N°7673 - Oauth2 for webhook * N°6088 - New attribute AttributeEncryptedPassword * N°7932 - Add english (GB) translation to iTop * Add EN GB dict file (#5) |
| 2024-09-03 | 1.2.3 | * N°7780 - 'allowed_login_types' order doesn't work for authentification with OpenID |
| 2024-08-02 | 1.2.2 | * N°7582 - Be able to tune debug configuration from UI |
| Not published | 1.2.1 | * N°7088 - Authentification OAUth2 with
Keycloack * N°6346 - combodo-hybridauth : update library for php 8.0 compatibility * N°4473 - Add delegated authentication (OpenID) configuration GUI |
| 2023-11-28 | 1.2.0 | * N°6556 - Add possibility to customize display of login buttons |
| 2023-07-13 | 1.1.2 | * N°6509 - Remove tests folder from builds |
| 2023-07-05 | 1.1.1 | * N°6369 Fixing warnings when configuration is
missing * Updated german translations by Lars Kaltefleiter |
| 2022-12-02 | 1.1.0 | * Compatibility with iTop 3.0 |
| 2019-08-27 | 1.0.0 | * First version |
Limitations
There is no mapping capability for contact provisioning.
This capability may not work if you have changed the default datamodel
Requirements
You have to configure the iTop application on your Identity provider to allow communication between iTop and this one. Look at your Identity provider documentation for more details.
Installation
Use the Standard installation process for this extension.
Configuration
First, you have to configure the iTop provider on your identity provider (Google, Facebook …)
-
The iTop landing page to provide to your Identity provider is:
<itop url>/env-production/combodo-hybridauth/landing.php
Once iTop is configured on Identity Provider side you can follow below steps
-
open the file 'config-itop.php'
-
add to the
allowed_login_typesparameter, the corresponding provider in the form of hybridauth-<provider name>
- config-itop.php
-
allowed_login_types => 'form|hybridauth-Facebook|hybridauth-Google|hybridauth-MicrosoftGraph|basic|external',
form must remain the first, for all the others to
be proposed to the user.
If an hybridauth option is entered first, then the login page
directly jump to the remote provider login page. basic
must be left in the list for REST to still work.
-
Customize OpenID authentication/login screen/ provisioning in a dedicated section
combodo-hybridauth.
In the providers section you can configure several providers. The “enabled” flag allows to activate the each authentication provider or not
Authentication Configuration
| parameters | description | values | global | configurable on IdP level |
| enabled | define wether the provider is enable or not. Caution you also have to remove the configuration from allowed_login_type, else the button remain on the authentication form | true or false | no | yes |
| keys | openid authentication fields like application id / secret | array of parameters (see examples below) | no | yes |
| debug | active the logging mode. All logs are written in the file log/hybridauth.log under iTop directory | true or false | yes | no |
Example: a configuration in which Google is configured but deactivated and MicrosoftGraph is activated:
- config-itop.php
-
'combodo-hybridauth' => [ 'debug' => true, 'providers' => [ 'Google' => [ 'enabled' => false, 'debug' => true, 'keys' => [ 'id' => 'your-google-client-id', 'secret' => 'your-google-client-secret', ], ], 'MicrosoftGraph' => [ 'enabled' => true, 'debug' => false, 'keys' => [ 'id' => 'xxxx-xxxxx-xxxxx-xxxxx', 'secret' => 'xxxxxx', ], ], ], ]
Login screen UI customization
| parameters | description | values | global | configurable on IdP level |
| label | label used on the authentication button for the corresponding provider. Use the default one if not set | no | yes | |
| tooltip | tooltip displayed when the use move over the button for the corresponding provider | no | yes | |
| icon_url | a url, a path to the icon in iTop or a fontawesome | exemples https://itop url/images/icon.png or images/icon.png or fas fa-key | no | yes |
Since version 1.2.0 (included in iTop pro 3.1.1) it is possible to customize the label, tooltip and icon on the login screen buttons. For example, if you would like to change the label and the icon to connect to google provider you can replace de default button by the one below

Define in module section theirs settings:
- config-itop.php
-
'combodo-hybridauth' => array ( 'debug' => false, 'synchronize_user' => false, 'synchronize_contact' => false, 'default_organization' => '', 'default_profiles' => ['Portal User'], 'providers' => array ( 'Google' => array ( 'enabled' => true, 'label' => 'Login like a bear', 'tooltip' => 'Login with your paw', 'icon_url' => 'fas fa-paw', 'keys' => array ( 'id' => 'your-google-client-id', 'secret' => 'your-google-client-secret', ), ), ), ),
In this case, you will see on the button the label you set +
provider name (automatically added after your label).
If you want to hide provider used to connect, you will need to use
dictionary entry in your configuration file and set values in all
languages you used to this dictionary entry.

- config-itop.php
-
'combodo-hybridauth' => array ( 'debug' => false, 'synchronize_user' => false, 'synchronize_contact' => false, 'default_organization' => '', 'default_profiles' => ['Portal User'], 'providers' => array ( 'Google' => array ( 'enabled' => true, 'label' => 'Google:HybridAuth:Login:SignIn', 'tooltip' => 'Login with your paw', 'icon_url' => 'fas fa-paw', 'keys' => array ( 'id' => 'your-google-client-id', 'secret' => 'your-google-client-secret', ), ), ), ),
Provisioning Configuration
Below iTop objects can be created/updated when connecting through Oauth2 provider via email/login reconciliation.
In other words user logs in via Identity Provider server. Then all fields associated to authentified user are used to create/sync up below object fields. Afterwhile user is connected into iTop with this new updated account (user+person).
-
User (
login,person_id) -
Person (
first_name,name,email,phone) -
Profiles (linked to user via
profile_list) -
Organization (linked to Person object via
org_id):
New in 1.2.4 : Organization assigned to created Person is either coming from service provider either by configuration (fallback).
-
Allowed Organization (linked to User object via
allowed_org_list)
| parameters | description | values | global | configurable on IdP level |
| synchronize_contact | define if contact provisioning is active, recommended if you have configured user provisioning | true or false | yes | no |
| synchronize_user | define if user provisioning is active | true or false | yes | no |
| refresh_existing_contact | (New in 2.0.0) define if contact provisioning can update person (and associated organization) | true or false | yes | yes |
| refresh_existing_user | (New in 2.1.0) define if user provisioning can update user (and associated profiles/allowed organizations) | true or false | yes | yes |
| default_organization | default organization used to create a contact | an iTop existing organization name | yes | yes |
| default_profile | profile name given automatically by default | 'profile name' | yes | yes |
| default_profiles | profile names given automatically by default | ['profile name1', …, 'profile nameX'] | yes | yes |
| default_allowed_orgs | (New in 2.1.0) allowed organizations attached to user | an array of organization names | yes | yes |
| groups_to_profiles | (New in 2.1.0) matching table between IdP keys and iTop profiles | empty (no matching) | no | yes |
| profiles_idp_key | (New in 2.1.0) key used to fetch profiles in IdP Oauth2 response | groups | no | yes |
| profiles_idp_separator | (New in 2.1.0) define if profiles IdP value should be split and set a proper separator (ie ',') | no value (means no split) | no | yes |
| groups_to_orgs | (New in 2.1.0) matching table between IdP keys and iTop organizations | empty (no matching) | no | yes |
| allowed_orgs_idp_key | (New in 2.1.0) key used to fetch profiles in IdP Oauth2 response | allowed_orgs | no | yes |
| allowed_orgs_oql_search_field | (New in 2.1.0) Use this field to search allowed organization by another attribute than 'name' | name | no | yes |
| allowed_orgs_idp_separator | (New in 2.1.0) define if allowed organization IdP value should be split and set a proper separator (ie ',') | no value (means no split) | no | yes |
| org_idp_key | (New in 2.1.0) key used to fetch organization in IdP Oauth2 response | organization | no | yes |
| org_oql_search_field | (New in 2.1.0) Use this field to search organization by another attribute than 'name' | organization | no | yes |
Example : Google IdP with provisioning enabled at first connection only. it describes how to use different profile and organization for a given provider.
- config-itop.php
-
'combodo-hybridauth' => [ 'debug' => false, 'synchronize_user' => false, 'synchronize_contact' => false, 'default_organization' => 'GlobalOrg', 'default_profiles' => ['Configuration Manager'], 'providers' => [ 'Google' => [ 'keys' => [ 'id' => 'id', 'secret' => 'secret', ], 'enabled' => true, 'synchronize_user' => true, 'synchronize_contact' => true, 'default_profiles' => ['PortalUser'], 'default_organization' => 'IT Department', ], ], ],
Example: profile synchronization with OktaOIDC (New in 2.0.0 )
Here iTop objects are created at first connection and updated each time user logs in iTop based on IdP up-to-date user data.
In below configuration:
-
if OktaOIDC sends sp_id1 group, then user will have “Configuration Manager” profiles. his previous profiles will be removed.
-
if OktaOIDC sends sp_id2 group, then user will only “Portal power user” and “Portal user” profiles.
-
if OktaOIDC sends sp_id1 and sp_id2 groups, user will have the 3 profiles.
-
if there is no profile matching with the groups returns by hybridauth JSON output, then connection to iTop is refused (user is considered without any grant access) and iTop user is saved with default profiles (if there are some configured)..
- config-itop.php
-
'combodo-hybridauth' => [ 'debug' => true, 'synchronize_user' => true, 'refresh_existing_user' => true, 'refresh_existing_contact' => true, 'synchronize_contact' => true, 'default_organization' => 'demo', 'default_profiles' => ['Portal User'], 'providers' => [ 'OktaOIDC' => [ 'enabled' => false, 'debug' => true, 'keys' => [ 'id' => 'your-id', 'secret' => 'your-secret', ], 'groups_to_profiles' => ["sp_id1" => "Configuration Manager", "sp_id2" => ["Portal power user", "Portal user"]] ] ], ],
NB: profile part of JSON OktaOIDC response is already an array of values.
Example: profile synchronization with a specific key coming from Json Keycloak response
In this case Keycloak provides profile in another key as a string. iTop explodes profiles via a configured ',' separator.
- config-itop.php
-
'combodo-hybridauth' => [ 'debug' => true, 'synchronize_user' => true, 'refresh_existing_user' => true, 'refresh_existing_contact' => true, 'synchronize_contact' => true, 'default_organization' => 'demo', 'default_profiles' => ['Portal User'], 'providers' => [ 'Keycloak' => [ 'enabled' => false, 'debug' => true, 'keys' => [ 'id' => 'your-id', 'secret' => 'your-secret', ], 'profiles_idp_key' => 'profiles', 'profiles_idp_separator' => ',', 'groups_to_profiles' => ["sp_id1" => "Configuration Manager", "sp_id2" => ["Portal power user", "Portal user"]] ] ], ],
Example: allowed organization synchronization with a specific key coming from Json Keycloak response
In this case Keycloak provides organization in
allowed_orgs key as a string. iTop explodes
organization named via a configured ',' separator.
- config-itop.php
-
'combodo-hybridauth' => [ 'debug' => true, 'synchronize_user' => true, 'refresh_existing_user' => true, 'refresh_existing_contact' => true, 'synchronize_contact' => true, 'default_organization' => 'demo', 'default_profiles' => ['Portal User'], 'providers' => [ 'Keycloak' => [ 'enabled' => false, 'debug' => true, 'keys' => [ 'id' => 'your-id', 'secret' => 'your-secret', ], 'allowed_orgs_idp_key' => 'allowed_orgs', 'allowed_orgs_idp_separator' => ',', 'groups_to_orgs' => ["sp_id1" => "Demo", "sp_id2" => ["My organization", "IT Organization"]] ] ], ],
Usage
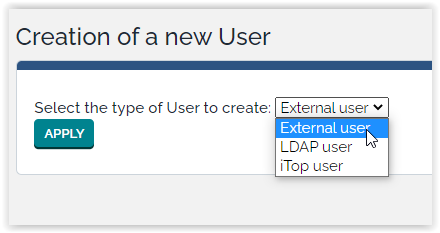
If you don't use the automatic provisionning, you have to create in iTop SSO users using the type External user when prompted for a “New user Account”:
Once configured, the Login form will look like
Questions & Answers
Q: Can I mix OpenID Connect and a captcha?
A: Yes this is possible using the Combodo's customer extension
Brute Force Protection.
Q: What is Hybridauth, OpenID Connect and
OAuth2?
A:
-
Hybridauth is the PHP library used by iTop to run the OpenID Connect protocol
-
OpenID Connect is the 3rd version of the OpenID protocol, it uses OAuth2, it's a protocol used exclusively for Authentication and user provisionning
Q: How to fix when consent form always displayed with
Google/MSGraph
A: This regression (due to N°8235) impacts version 1.2.4
only Please upgrade extension version. Otherwise follow
workaround procedure.
Even when remaining connected on Identity provider (Google/MSGraph only), consent form is proposed each time you click on login button. in versions = 1.2.4, the form was not displayed and user was immediately logged in.
Workaround (Google/MSGraph only): add authorize_url_parameters section as proposed in below example
'combodo-hybridauth' => array (
...
'providers' => array (
'Google' =>
array (
'enabled' => true,
'authorize_url_parameters' =>
array (
'prompt' => '',
),
...
Q: Can we implement several connexion for a given
provider to implement several tenant?
A: Since version 1.2.0 (inclued in iTop pro 3.1.1) this is possible
to configure several connexion to different tenant using the same
provider.
In the example below we configure connexion with MicrosoftGraph to TENANT1 and TENANT2
You have to configure the module combodo-hybridauth to define 2 providers using the same adpater (method to access the provide). It is MicrosoftGraph in our example.
The code TENANT1 and TENANT2 are the idenfier that will be used in the variable allowed_login_type to allow those connexions
You can specify application id and secret corresponding to your tenant and define label, tooltip and icon specific to help the user to chose the good connexion method.
- config-itop.php
-
'combodo-hybridauth' => array ( 'debug' => true, 'synchronize_user' => false, 'synchronize_contact' => false, 'default_organization' => '', 'default_profiles' => ['Portal User'], 'providers' => array ( 'TENANT1' => array ( 'adapter' => 'Hybridauth\\Provider\\MicrosoftGraph', 'label' => 'Authentification On Tenant 1', 'tooltip' => 'Connexion from O365 - Tenant 1', 'enabled' => true, 'keys' => array ( 'id' => 'MyApplicationIdOnTOnMyTenant-1.fr', 'secret' => 'MySecretOnMyTenant-1', ), 'synchronize_user' => true, 'synchronize_contact' => true, 'tenant' => 'MyTenant-1.fr', 'default_organization' => 'MyCompagny', ), 'TENANT2' => array ( 'adapter' => 'Hybridauth\\Provider\\MicrosoftGraph', 'label' => 'Authentification On Tenant 2', 'tooltip' => 'Connexion from O365 - Tenant 2', 'enabled' => true, 'keys' => array ( 'id' => 'MyApplicationIdOnTOnMyTenant-2.fr', 'secret' => 'MySecretOnMyTenant-2', ), 'synchronize_user' => true, 'synchronize_contact' => true, 'tenant' => 'MyTenant-2.fr', 'default_organization' => 'Demo', ), ), ),
In this case, the provider 'TENANT1' gives access to iTop with a MicrosoftGraph connexion to MyTenant-1.fr, and the provider 'TENANT2' to MyTenant-2.fr
in your configuration file, you have to add values hybridauth-TENANT1 and hybridauth-TENANT2 in field allowed_login_types:
- config-itop.php
-
'allowed_login_types' => 'url|form|hybridauth-TENANT1|hybridauth-TENANT2|external|basic',
https:<itop server>/pages/UI.php?login_mode=hybridauth-TENANT1</note> if you have a large number of tenant, for instance one by customer, you can use this syntax in an HTML page where you display the URL for each tenant in order to route the user to the good one