Password Expiration Management
🤦 🤦 🤦 Included in iTop Community from 3.1.0 😎 😎 😎
- name:
- Password Expiration Management
- description:
- Enforce password expiration rules (if configured) for local iTop accounts.
- version:
- 1.0.3
- release:
- 2025-01-25
- itop-version-min:
- 3.0
- state:
- Stable
- php-version-max:
- PHP 8.3
This extensions uses existing UserLocal fields to
implement a password expiration mechanism.
Features
-
A User manager can manually force one or multiple iTop users to change their password the next time they will connect to iTop.
-
An iTop administrator can force every local iTop users to change their password on a regular basis (configurable delay).
-
A User manager can create a User which can connect only once to iTop
-
For such user, the password is automatically set to a random value after the first successful login.
-
Such user password even if stolen can never be reused.
-
It's usually set by a script, to give a single access to someone and track separately when and to whom that access was given
-
Revision History
| Version | Release Date | Comments |
|---|---|---|
| 2025-01-25 | 1.0.3 | * N°7932 - Add english (GB) translation to iTop * N°7846 Suppress risky syntax with DateTime::modify |
| 2024-08-05 | 1.0.2 | * N°6899 - Update chinese translations thanks to @bdejin |
| 2023-06-29 | 1.0.1 | * Updated german translations by Lars Kaltefleiter |
| 2021-08-06 | 1.0.0 | * First version |
Limitations
Requires iTop 3.0 or newer.
There is no warning/reminder to the user that her/his password is about to expire.
Configuration
| Parameter | Type | Meaning | Default value |
|---|---|---|---|
| password_expiration_delay | Integer | Number of days for which the password remains valid. After this delay the end-user (for who the rule is “can expire”) will be forced to change her/his password the next time they log-in. Zero (or a negative value!) means no expiration. | 0 |
Usage
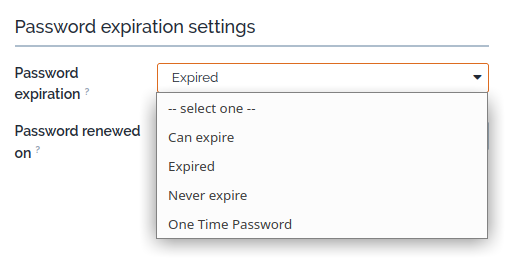
Edit the user accounts and set the appropriate policy for each user:
| Password expiration | Behavior |
|---|---|
| Never expire | The password never expires. This is the default behavior. Use this for scripts/machine accounts. |
| Can expire | Assuming the configuration parameter password_expiration_delay is set to a positive number, then the user password will expire after that number of days from its last change. If the user connects to the application and the password is expired, the user is immediately redirected to the “Change password” page with a message indicating that the password has expired and must be changed before continuing. |
| Expired | The password is considered as expired immediately.
The next time the user connects to the application, she/he is
redirected to the “Change password” page. Once the password is modified, the user flag is automatically set to “Can expire”. |
| One-time password | The password is valid just for one session. The
password will be automatically set to a random value just after the
first successful connection. Neither an User Manager nor an Administrator can set his/her own account with this value as it would deny them iTop access. |
User experience
When a user password is expired (either because an administrator
set it manually to expired or because the password was created or
last changed more than password_expiration_delay days
ago), then the next time that user will try to connect, he will be
immediatly asked to change his password and of course the new
password will have to be compliant to the password policy.
-
The new password must be different from the previous one
-
As previous passwords are not kept, there is no further checks which would prevent password rotation
-
If the User
Password expirationfield was set to Expired it is switch back to Can expire once password has been changed.
Enforcing password policy
You have defined password policies, but as this does not apply to existing passwords, you can massively update your iTop users to force them to change their password, and so guarantee that their new password will be compliant with your policy.
Force password renewals
Let's assume you want to force your users to change their password at least once a year
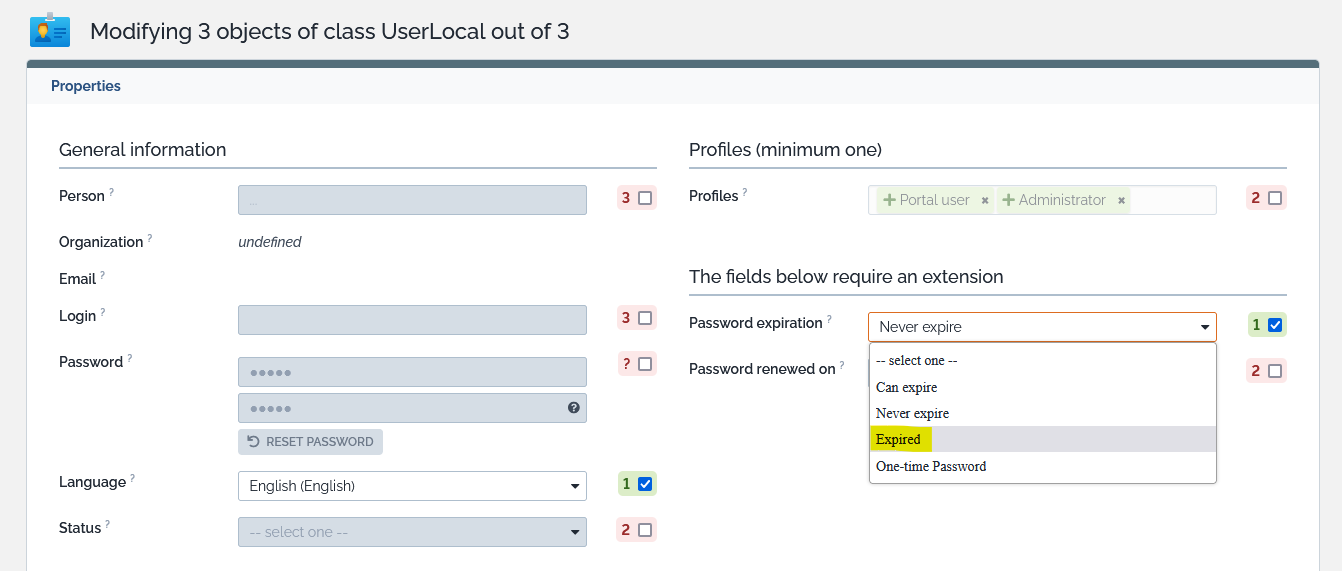
1. Do a bulk modification of all your iTop users to set their
Password expiration to Expired or Can
expired depending on if you want them to change it now or
within a year
2. Set in the Configuration file, the
password_expiration_delay parameter
'combodo-password-expiration' => array( 'password_expiration_delay' => 365, // Force password change every year ),